|
|
|
How to find a virus aka how to analyze a virus
There are several ways to find and analyze a (windows) virus.
You know what behaviour of your system is normal
- you know the programs you installed on your system
- you know all the processes which typically run on your system
- typical load on your system (harddisk activity, CPU load)
=> You will be able to compare the current behaviour with a unusual behaviour (e.g. harddisk activity even if you do nothing with your system, additional files and/or processes)
Tools for that:
- HijackThis (original >here<, but further development was done by Trendmicro, download >here<)
- ESET SysInspector (see >here<)
- Process Explorer (originally made from SysInternals, taken over by Microsoft, still very helpful, download >here<)
- TaskInfo (similar to Process Explorer, more info at a glance, see >here< for more info)
- RootKit Revealer (orig. from SysInternals, taken over by Microsoft, still very helpful, download >here<)
- Rootkit Unhooker (see >here< ... unfortunately only on archive.org now, convenient GUI, but no further development, download also >here<, developer went to Microsoft)
- Visit Comparitech's >free root kit removal article< for another list of rootkit detection programs
- GMER (see >here<, less convenient, but still supported and developed further)
- A handy tool called >svchostviewer<
- Also take a look at all your installed driver - with >DriverView<
- A very useful system monitor tool, >Moo0 System Monitor<, also helpful for a search for a performance break...
- >DiskMon< from the Sysinternals guys (harddisk activity)
- Moo0's >File Monitor< (shows open files)
- NirSoft's >Opened Files View<
- Your Windows build in tool msconfig.exe (more info - see >here<)
- Your build in tool services.msc (to get an overview about all installed services)
- Your brain ;-)
Also, if you identified a suspicious file, you can analyze the file by using several tools. Typically a normal user trust on his Antivirus-program only. That's really not enough, because these programs do not know new viruses until somebody found them and publish it. Some Antivirus-programs offer additional features like heuristic detection and a guard for registry changes. Heuristic is often overstrained, if too weak, doesn't detect much, if too strong, detect even wanted, harmless programs. And the user can't decide which changes are needed and which changes are unwanted, if a guard reports every change.
There was a real useful program (at least for 32bit Windows), but it's not very often mentioned: "API Guard" from Jakub Debski
Source code is even supplied too, it has a simple interface, and it works.
It controls API call, so you can allow or disallow any action just with a checkbox, and run a suspicious file in a controlled shell. This does not work with more sophisticated call methods of system functions, but it's worth a try - possibly in a virtual machine, so if nothing is blocked with the tool itself, your real system is still not affected.
Newer but also very useful: >Sandboxie<. More sophisticated compared to API Guard, but also larger. It stores changes to the file system and registry in his own area.
If you want to find out, if any antivirus program on the market detects anything bad, try to upload the file at >Virustotal<.
Also, there are some approaches to analyze it automatically via sandboxes or modified x86 emulators.
Try >Joebox< (a secure sandbox application) or >Anubis< (analyzing unknown binaries) to get an overview of the used API calls or used files/registry entries.
Promising is also "Zerowine", a project which uses Wine to let the malware run in a controlled way.
To detect exepacked viruses, try my program >here<.
Take a look at the Cryptographic Implementations Analysis Toolkit also, and a small tool, called ENT, is worth to be tested, too. Both can display the entropy of a file in a graphic/in an image file.
To look into PE header and related infos, use >PPEE (Professional PE file Explorer)< - very useful !
Also very helpful: CFF Explorer, it can show you PE infos but can also disassemble sections. Also good to change parameters like Large Address Aware bit (to give programs more than 2GB RAM when running with x64 Windows).
To unpack packer like FSG 2.0, try >FUU< (Faster Universal Unpacker).
Many script kiddies are coding VBA and compile it, so to decompile it, try a decompiler, an overview can be found at woodman.com >here<
To analyze program code, you need some knowledge of assembly language. But this is not rocket science.
- A very good disassembler tool: IDA Pro, see >here< for more details
- A discontinued disassembler, but still useful: >W32Dasm<
- A very good 32bit debugger: >OllyDbg<, even API spying is possible (feature is called "Intermodular Calls")
- A promising x64 capable debugger: >x64dbg<
- A very good (free) debugger also: >Syser Win32 debugger<
- If you need to debug also deep into the kernel (Ring 0), you have to use >Syser Kernel Debugger< - looks like this:
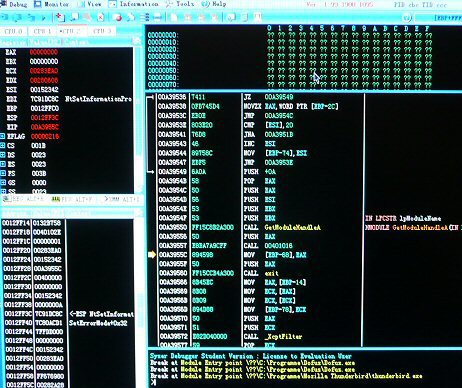
(Screenshot from Syser Kernel Debugger,
always at your service with Ctrl F12 ;-)
Update: Unfortunately Syser seems to be no more available meanwhile. Try out >Bugchecker< as another "SoftIce" replacement. Or >ArkDasm<.
Please take also a look at >Immunity Debugger< , and don't forget the "volkswagon" of the debuggers, >Microsoft's WinDbg<.
- A very good debugging tool was >SoftIce<, a part of a driver development suite, unfortunately it's >no more available since 2006<.
Really interesting:
How to hide your process from all above mentioned tools.... ok, except from the rootkit discovering tools, but from all others:
Hackers Defender 1.0 ... it was published in 2004 but it is still worth to analyze and learn from it (source included, written in Delphi).
This virus will be detected for sure from all known virus scanner - so don't worry about my offer, IT IS FOR EDUCATIONAL PURPOSES ONLY. The archive is password protected (password = 'rootkit'). You can d/l it from my local mirror >here<.
Also an interesting web site: >GreyHatHacker.net< with many hints about (current) exploits/weaknesses and how to mitigate them.
If you're still interested how exploits work (and then how to avoid them), read all parts of the >really good tutorial at corelan.be<.
|
|