| EXE-Packers (for Windows) are very often used for "scrambling" malware !
What does this mean - is that a danger ?
Yes, of course. Typically someone develops a program with a compiler (like Delphi or Visual C++). It is easy to look into that compiled files with a hex editor (or a program like UltraEdit).
If that program is malware, a signature is taken (a byte sequence or a hash value) to find the program again.
Now if someone plan to hide this or to make it very difficult to analyze it, he uses an executable packer/compressor, it makes the program smaller and not anymore readable by a hex editor.
A well known program is UPX for example, you can find it even with source code on Sourceforge here.
Unfortunately very often the antivirus vendors (e.g. Symantec) do not implement unpackers nor the detection that the suspicious file is packed by an exepacker program.
To get all these "candidates" on your own harddisk, I developed an exepacker files searcher program.
Screenshot:
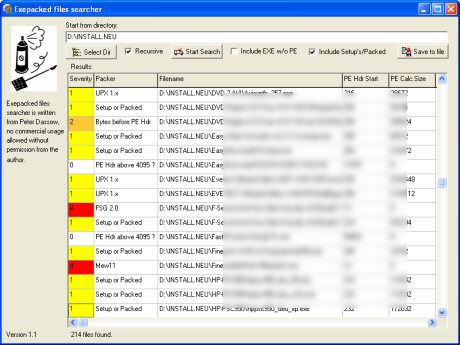
You can choose the starting directory and after the search was done, you can get additional info with a doubleclick on the (filled) table. At the moment, the program is able to find 10 exepacker:
UPX 1.x to 3.x (all versions now tagged as 'UPX')
FSG 2.0
RLPack
PECompact 2
Petite 2 (and probably also older versions)
UPack
Aspack 2
Mew11
NSPack 3
Packers like ExeCryptor 2
(few bytes inspected before PE Hdr starts)
It looks for some byte sequences at the beginning of the exe-file.
Also it checks a proper structure of an executable PE file.
If you know other exepackers which are spreaded widely, please send me an email (with an URL for downloading the packer).
I have changed the detection algorithm a bit since Version 1.004, more hierarchical, less chaotic ;-)
Also, since 1.004 there is a severity ranking and an additional info (starting position of PE header), also the ability to exclude DOS-like EXE-files without PE-Header.
In Version 1.1 I added size prediction (means the program will find with a rate of almost 100% any EXE-packed program, it's done by a summation of .text size, .data size and 'size of header'. The detection could be included with an additional checkbox.
I resized the program window to 800x600 pixels also.
Small bug fixed in 1.101, 'Save' now generates a correct comma separated file format, also I changed the detection of PECompact 2 files a bit to get more hits.
Changed UPX detection in v1.102 to a more generic approach, now it's tagged as 'UPX' only, regardless of the version (1.x-3.x).
Now it's possible to change the column width.
I am planning to implement a kind of entropy analyzing function also, because my program will not be able to detect execrypted but correct sized programs, only exepacked ones.
You can download the sixth revision of the program here (271KB).
If you are interested in the source (Object Pascal), write me an email.
Meanwhile there are many tools available to detect and analyze executable files, a very good overview of all so far offered programs can be found here. Also, please visit my "Find and analyze a virus page" here.
Beside this, I developed an other program to control the startup service sequence:
SvcOrder - Shows the service start order of Windows
There is no build-in possibility to show the Windows service order used during OS startup.
To solve this, I developed a small utility (still in alpha state) in Delphi 6.
See this screenshot:
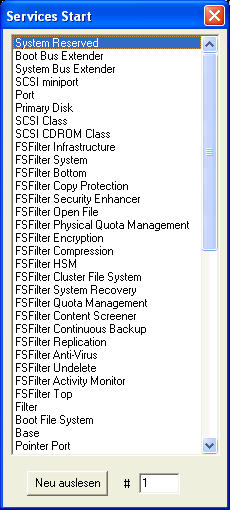
Basically it reads a structure from the registry.
Download the program (will be updated soon).
The next version will show more detailed information about the
ServiceGroup, I hope to give also a possibility to manipulate the
startup order of the Windows Services soon.
|